- ByteSize
- Posts
- Mona Lisa frowns at password clowns while malware prowls around
Mona Lisa frowns at password clowns while malware prowls around
PLUS: Amazon bullies Perplexity's shopping bot while IBM axes thousands and Epic high-fives Google...

It's 11/11. It’s time to make that wish, and then cable-manage your regrets!
The Ethernet turns 52 and your router is acting like it’s 92… On this day in 1973, Robert Metcalfe and David Boggs got their Ethernet network working for the first time at Xerox PARC. Fun fact: they originally wanted to call it "Alohanet" but realized nobody would take a Hawaiian-themed network protocol seriously in corporate America.
Today, Ethernet is everywhere—kind of like how reality TV was supposed to be a temporary fad, except instead of destroying civilization, it actually made our civilization possible. Wild how that works out.
Hackers Turn OpenAI Into Their Personal Command Center
Microsoft discovered a delightful new malware called "SesameOp" that uses OpenAI's Assistants API as its command-and-control channel. That's right—hackers are now using ChatGPT's infrastructure to boss around their malware, which is basically the tech version of using your mom's minivan for a heist. The malware doesn't even talk to ChatGPT; it just hijacks the same pipes that millions use to ask AI about their feelings.
The genius here is hiding in plain sight. Seeing "api.openai.com" in your network logs doesn't exactly scream "compromised system.” It just looks like Todd from accounting is asking ChatGPT to write another passive-aggressive email. Microsoft's hunting query to spot this is basically "look for weird processes talking to OpenAI," which feels like telling someone to watch out for suspicious activity at a Starbucks.
OpenAI has disabled the bad actor's API key, and the Assistants API gets deprecated in August 2026 anyway. But don't worry—criminals will find another trusted cloud service to turn into their getaway car. Maybe next time they'll use Spotify to coordinate cyber attacks, because apparently we live in the stupidest timeline.
Mona Lisa Frowns at Louvre Museum's Security Password
We’ve all heard about the October heist that saw $102 million in crown jewels stolen from the Louvre is looking less like Ocean’s 11 and more like the Three Stooges every day.
Well, it gets worse… It turns out the museum's video surveillance password was literally "Louvre." I'm not making this up. This is the same institution that houses the Mona Lisa, and they protected their security system with the creativity of a Windows 95 setup wizard.
According to French newspaper Libération, a 2014 cybersecurity audit found passwords like "LOUVRE" protecting critical systems, and “THALES" for accessing Thales software. (You can’t see me, but I’m shaking my monitor right now!) Yes… the museum was running Windows Server 2003 with security software from the same era, essentially protecting priceless artifacts with digital infrastructure older than some art itself. At this point, let’s just hire Paul Blart: Mall Cop to protect Fort Knox.
The thieves fumbled a crown during their escape and tried to light their mechanical lift on fire as a distraction. When your museum's cybersecurity is so bad that bumbling criminals in hi-vis vests can waltz out with nine-figure art collections, maybe it's time to hire someone who doesn't think "password123" needs more numbers.
Russian Spies Pack Malware Into Windows VMs
Russia's "Curly COMrades" group (yes, that's their actual name, because even cybercriminals have LinkedIn now) discovered they can hide malware inside Hyper-V virtual machines to bypass endpoint detection. They're creating tiny 120MB Alpine Linux VMs that run stealth reverse shells while your EDR software sits there like a golden retriever watching a magic trick.
The setup is actually clever—all malicious traffic appears to come from the legitimate host machine's IP address, so it looks totally normal. It's like wearing a suit to rob a bank… nobody suspects the person in business attire is up to no good. The VM hosts two custom implants called "CurlyShell" and "CurlCat," which sound like rejected Pokémon characters but are apparently quite effective at espionage.
This confirms what security folks have been saying: as endpoint security becomes more common, attackers just get better at hiding. It's an arms race, except one side is selling expensive software and the other side is using free virtualization to make that software completely useless.
⚙️ TOOL TIME
Sometimes You Just Want to Poke the Network
You know that “what happens if I click this?” urge that somehow ends with regret, documentation updates, and possibly a fire.
Yeah… we’ve all been there.
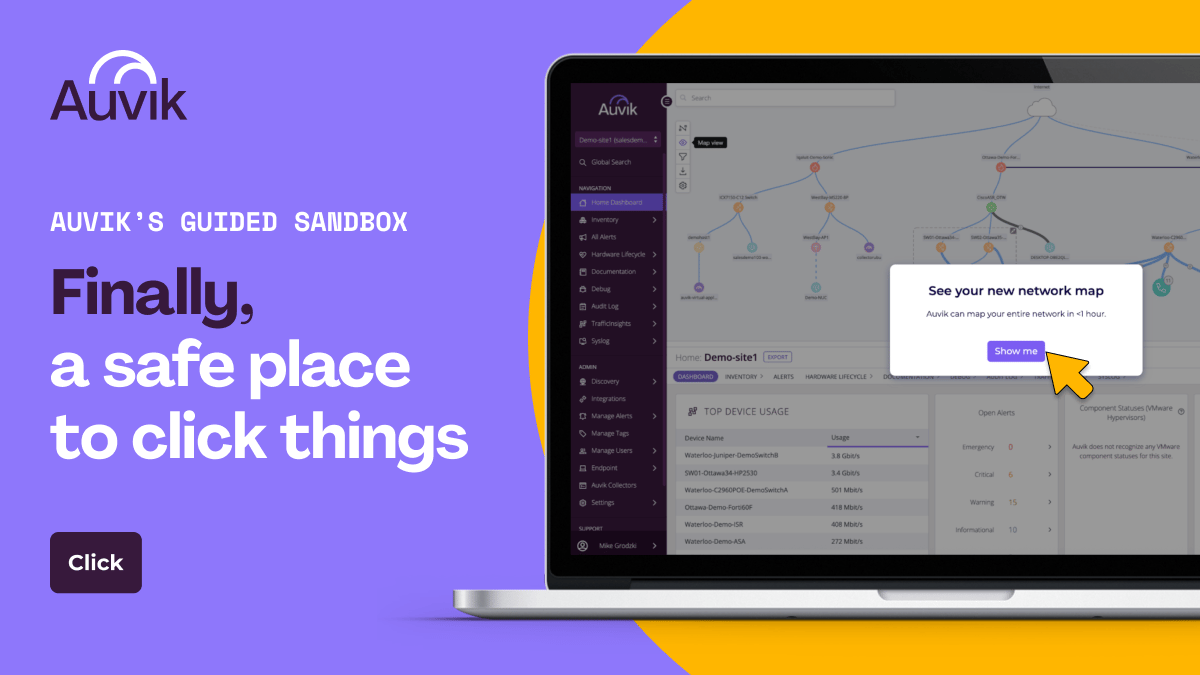
Enter Auvik’s Guided Sandbox, a safe demo environment where you can explore, click, and tinker to your heart’s content without accidentally nuking production.
No setup. No credentials.
CTA BUTTON: 🕹 Dig into Auvik’s Guided Sandbox
Inside the sandbox, you’ll see exactly why 80,000 MSPs and IT pros use Auvik’s network management software to:
Map, discover, and search any and all devices on the network
Get full specs, lifecycle data, and performance insights on every device
Spot problems fast with severity-ranked alerts
Poke around, explore, and watch Auvik do what your current tools say they can.
Auvik Network Management is a vendor-agnostic cloud-based network monitoring and management solution that enables fast out-of-the-box deployment for quick and automated network discovery. Auvik requires no service hardware or disruptive maintenance cycles and provides fast onboarding and training for new and existing users.
👨💻 JOB OPPORTUNITIES
The bank is looking for someone to lead vendor dispatches and manage stockroom assessments. In other words, you just need to make sure the office supplies don't achieve sentience and overthrow the financial system. ITIL framework knowledge preferred but not mandatory (they'll teach you to love acronyms).
The cloud-based SaaS company is hiring a director to manage a global service desk team while ensuring "world-class technical support." Translation: you'll spend your days explaining why turning it off and on again is still the first solution to 90% of tech problems.
San Francisco only, because apparently IT directors can't work remotely to manage...
*REMOTE* IT infrastructure. You’ll be driving enterprise AI programs while ensuring systems don't page you at 3 AM about themselves being broken.
🛩 INDUSTRY MOVES
Amazon threatens Perplexity over its shopping bot that doesn't identify itself as an AI agent. Bezos to Perplexity: “Either your bot wears a name tag, or it’s banned from the store like a 12-year-old trying to buy fireworks.”
IBM cutting several thousand jobs while executives promise "profitable infrastructure business this year.” Their strategy: automate empathy, offshore stress, and profit off survivor’s guilt.
Internet Archive survived major copyright battles but lost 500,000 books, proving that lawyers can destroy more culture than any natural disaster. Seriously… half a million of books gone because lawyers said “sharing” is only legal with Venmo attached.
Epic and Google settled their lawsuit with Android getting global changes and lower fees—victory through litigation remains America's favorite sport. Somewhere, a Fortnite skin just shed a joyful tear.

You’re back! It's your favorite silicon mascot here with another round of "What Fresh Hell Is This?" from the EE forums
Someone wants to implement AI into their Windows apps but doesn't know where to start. (Nobody does). It's like asking how to become TikTok famous… There's no manual. Just chaos, prayer, and a deep lack of shame.
Another poor soul is fighting with wget, trying to download files but getting error messages that look like my cat, Fez, walked across their keyboard. Windows file paths and Unix commands mixing about as well as orange juice and toothpaste.
We have a VMware converter error that's basically the digital version of "Does not compute." The server can't recognize the host type, which is IT speak for "Have you tried just buying new everything?"
Thanks for spending 11/11 with us! Go make a wish, close a ticket, and pretend it all balances out. We’re back next week with more bytes and fewer tangles.
Enjoyed the news? Discuss over on Experts Exchange.
Got news to share or topics you'd like us to cover? Send ‘em our way by responding to this email. We can’t wait to hear from you. Really.